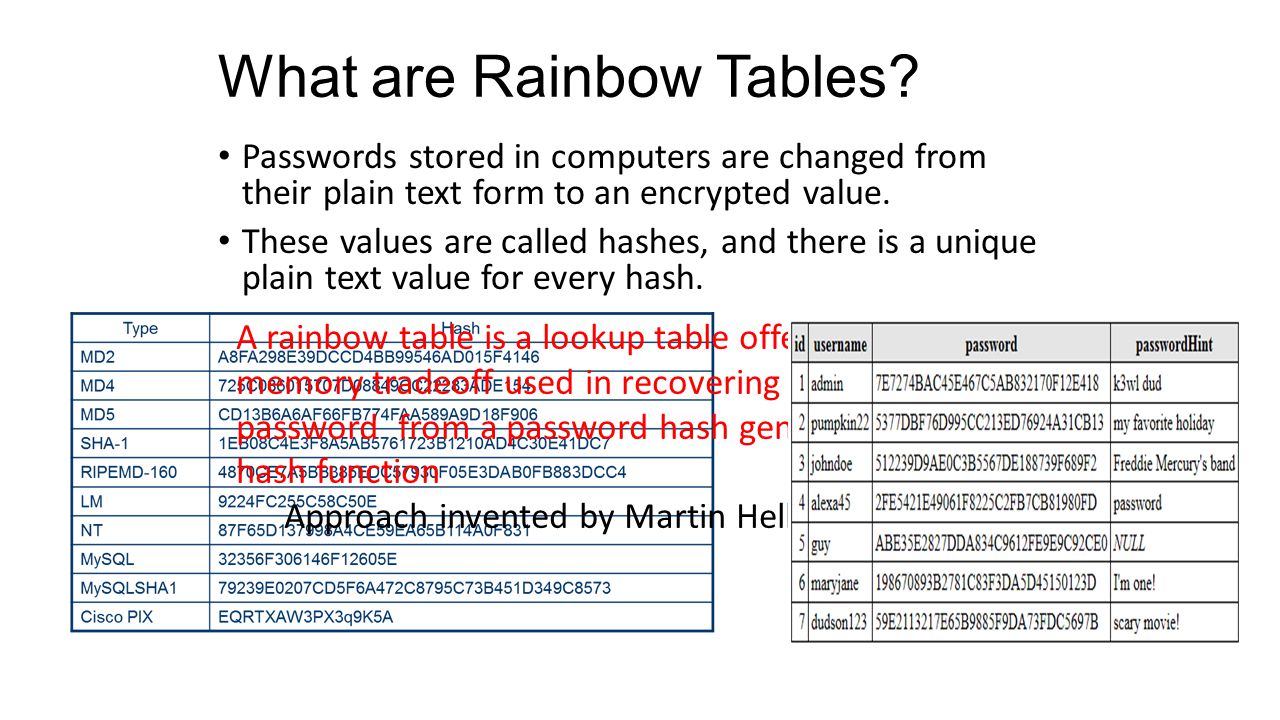
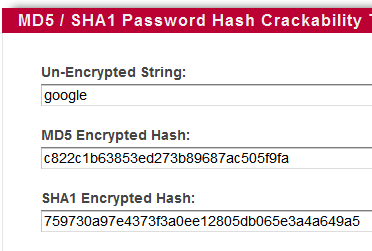
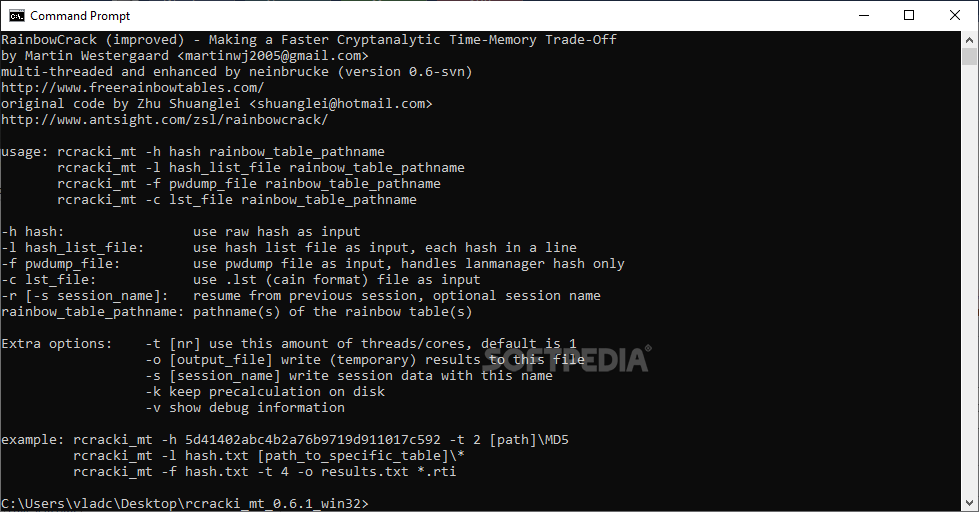
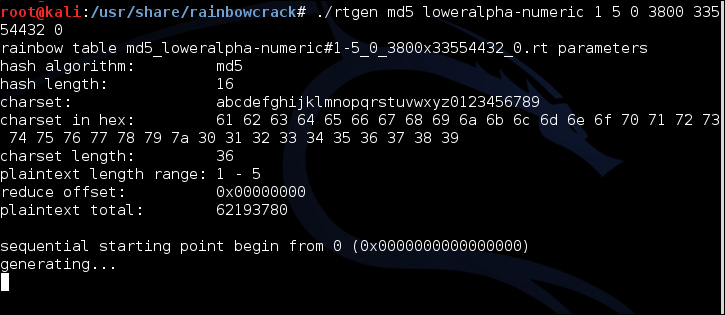
KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021
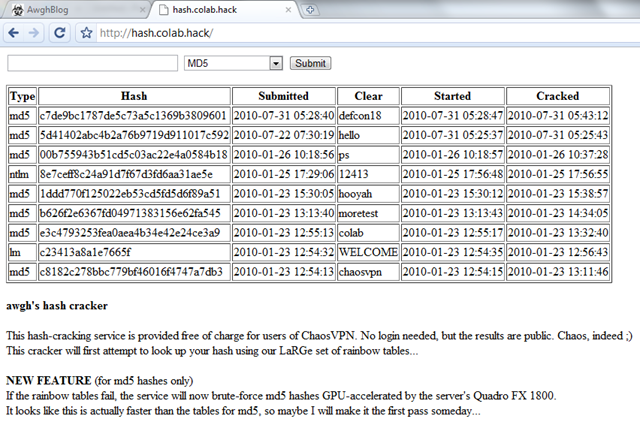
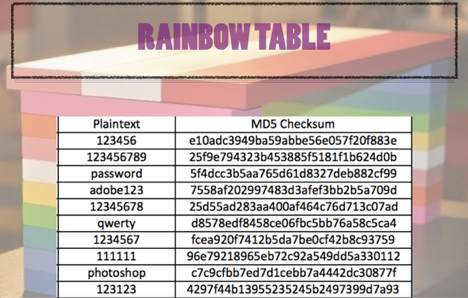
GitHub - AurelioDeRosa/Audero-MD5-Rainbow-Table: Audero MD5 Rainbow Table is a precomputed table, made of 11.110.097 entries, for reversing strings encrypted using the MD5 hash function.

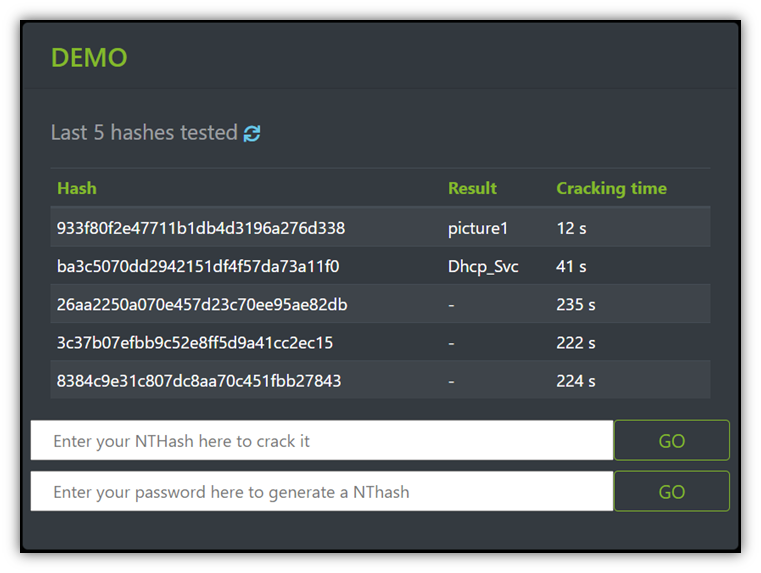
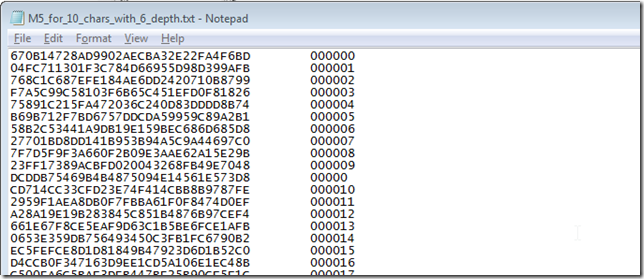
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo