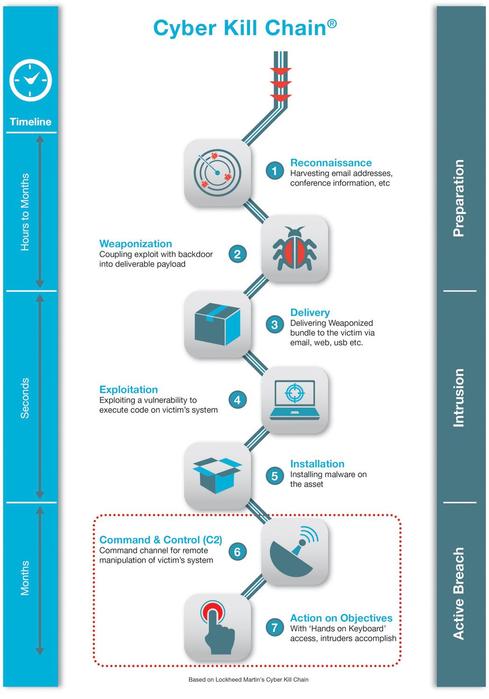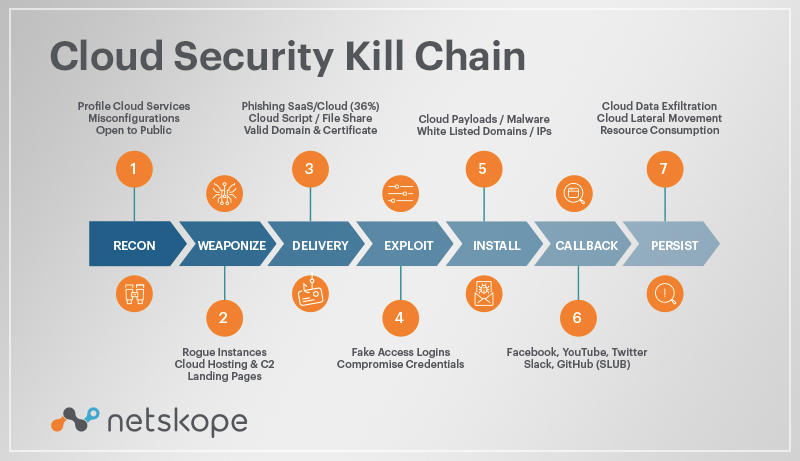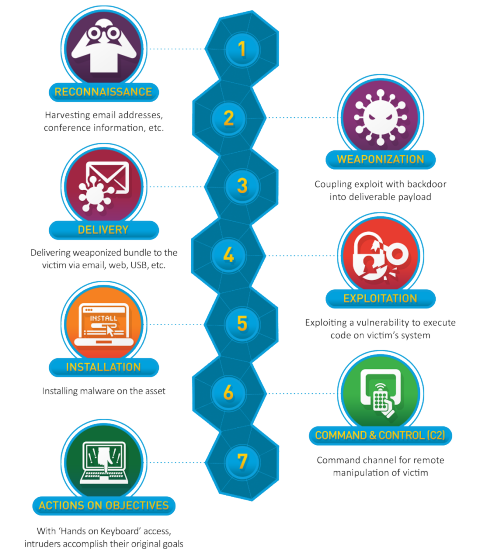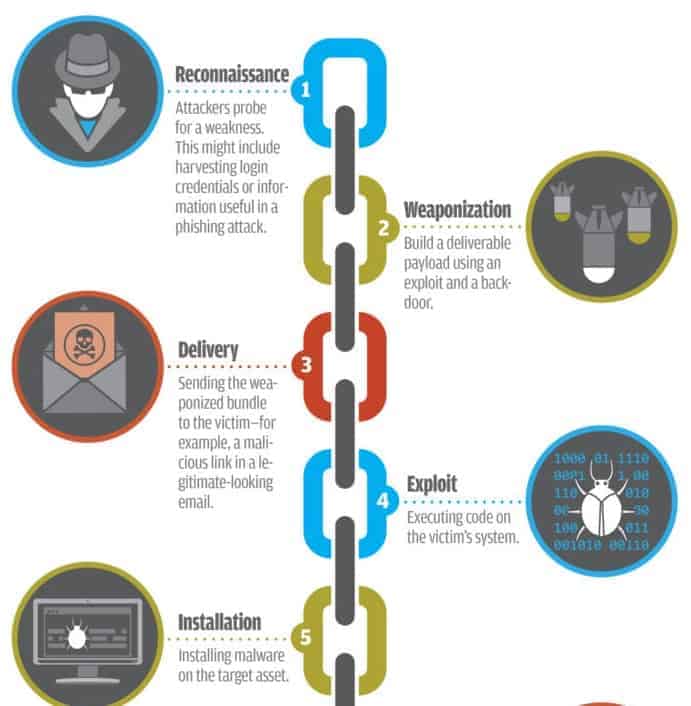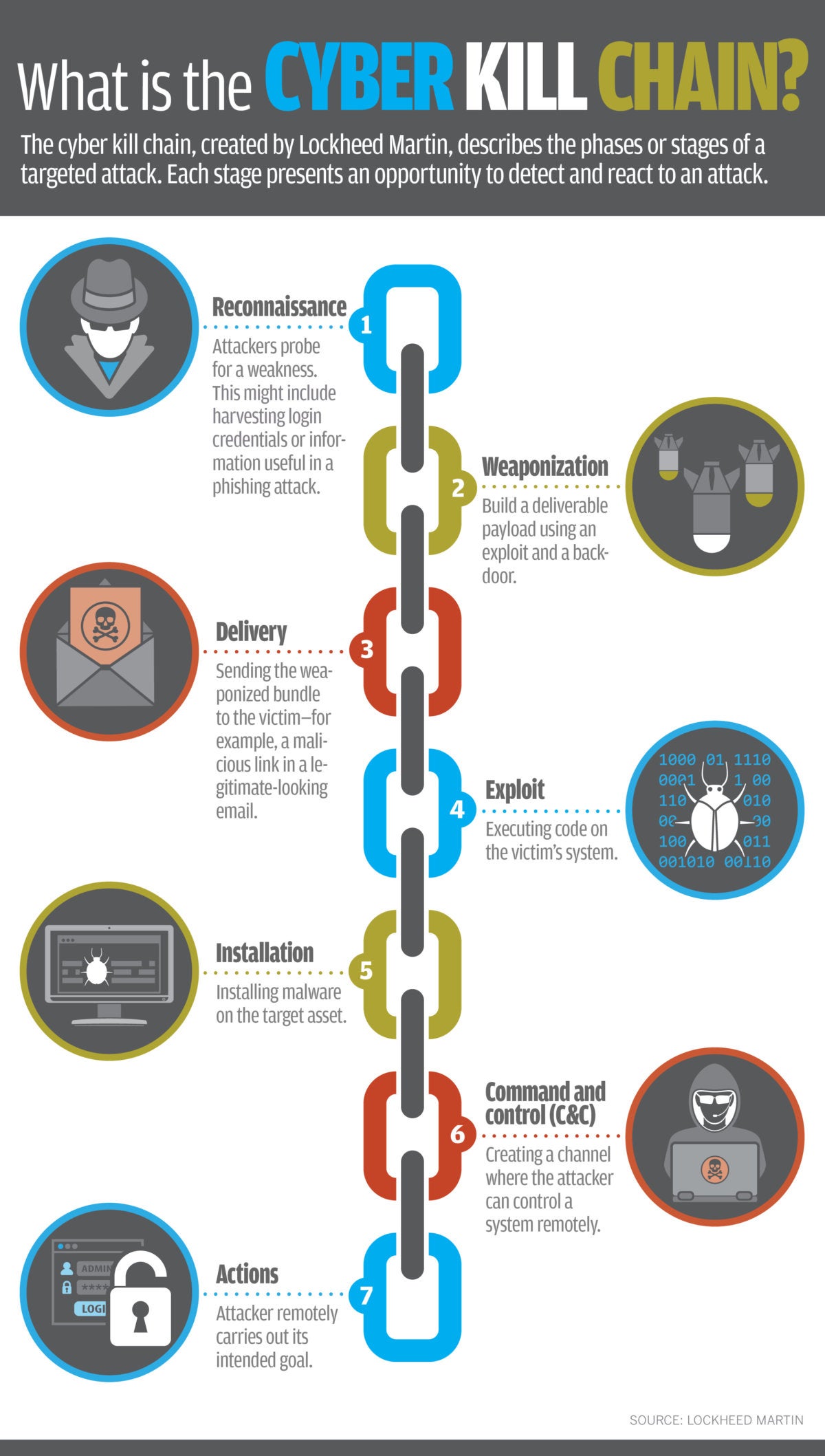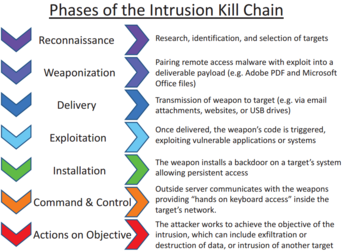
Rohan Amin on Twitter: "10 years ago this month, Eric Hutchins (aka @ killchain), @mikecloppert and I published a paper to share analytical tradecraft we had been using to defend networks against Advanced

Hillstone Networks intelligent Next-Generation Firewall: Detecting Post-Breach Threats Using the Cyber Kill Chain | Hillstone Networks

![PDF] Breaking the DDoS Attack Chain | Semantic Scholar PDF] Breaking the DDoS Attack Chain | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1dea6bdbf069a699856837abdb51c1d279695759/3-Table1-1.png)